Dark web markets such as Silk Road and Sipulitie have relied on Tor’s anonymity features for years. Despite the robust technology, human errors frequently leave traces. These traces can range from cryptocurrency transactions and communication metadata to actual data seized from servers.
Recent takedowns of these markets have exposed vulnerabilities in the dark web’s perceived anonymity. Let’s examine how law enforcement has been gradually dismantling this illusion of invisibility.
Fall of the Silk Road

The dark web seemed for a while at least some impenetrable underground fortress. This fortress already showed cracks after the FBI arrested Ross Ulbricht, at time one of the biggest names in the dark web, the creator of Silk Road. That website was the first modern darknet market, mostly used for drug trafficking, but there were speculations of worse things, which turned out to be true. Not only could you also order weapons, you could even hire hitmen, to only scratch the surface of what went on there.
Despite Ulbricht’s arrest in October 2013, the dark web’s perceived invulnerability persisted. The FBI’s method of infiltration was surprisingly low-tech: they staged a distraction in a library, executing a physical access attack on Ulbricht’s laptop. This in turn enforced the feeling of invulnerability. Despite the high-profile arrest, many believed that only through physical intervention could the dark web’s defenses be breached.
This persistence of perceived anonymity led to a false sense of security among dark web users, who continued to operate under the assumption that their digital footprints were untraceable. Indeed browsing the internet with Tor, and optimizing various settings such as disabling the browser’s JavaScript rendering, makes a trace harder to find.
However, as recent events have shown, this belief was far from reality. Long time before those high-profile cases, law enforcement has marked the dark web as a potential target, and while you can achieve near-anonymity there, traces are left beyond the Tor browser and the dark web itself.
The Fall of Bohemia/Cannabia
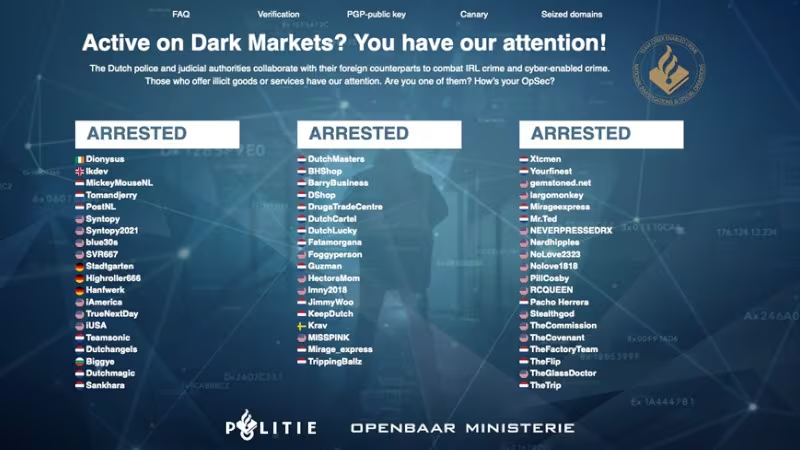
The Dutch police announced on Oct 8 a major victory against dark web crime. The website Bohemia and it’s sister website Canabia (two major dark web markets) were doing big business at their peak in 2023: about 67,000 illegal deals a month, worth up to €12 million. Late last year it was disclosed that the administrators pulled an exit scam, effectively running away with 5 million dollars.
The Dutch police identified several administrators and arrested two suspects, one in the Netherlands and another in Ireland. They also seized two vehicles and cryptocurrency worth €8 million.
Stan Duijf, head of the operations unit of the National Investigation and Interventions, made a statement:
Administrators, sellers and buyers of and on illegal marketplaces often believe themselves to be elusive to the police and the judiciary. By conducting criminal investigations and prosecuting these criminals, it becomes clear that the dark web is not at all as anonymous as users may think.
The fall of Sipulitie & Tsätti
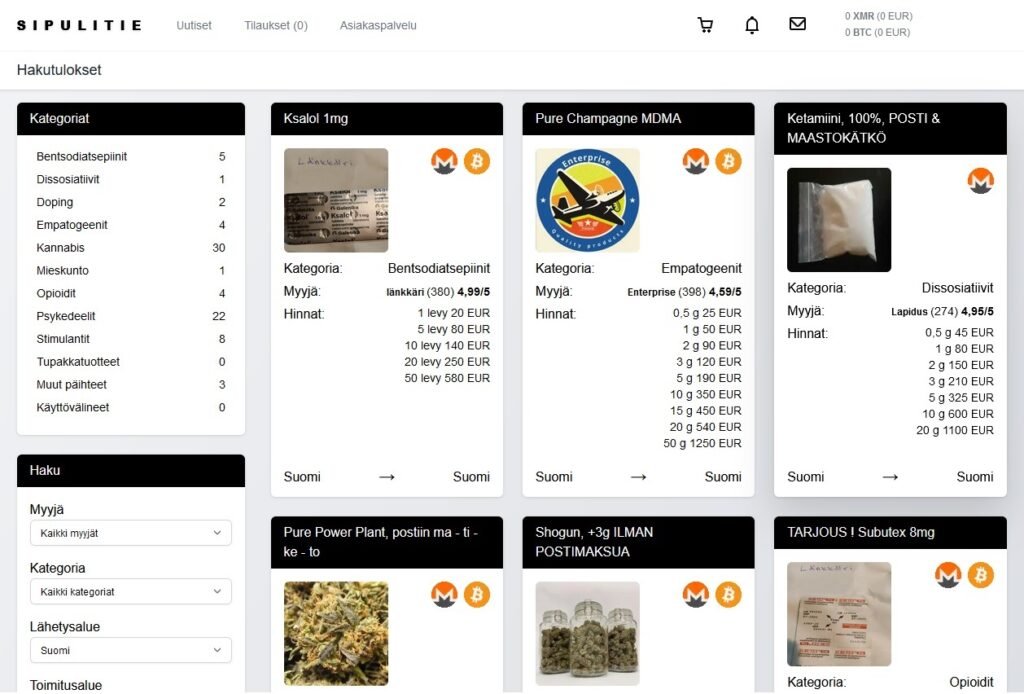
October was a great month for law enforcement in the war on the illegal trade on the dark web. Finnish Customs, Europol, Swedish Police and Bitdefender cooperation led to this significant operation, which also involved law enforcement agencies from Ireland, the United Kingdom, and the United States. The investigation began towards the end of 2023, culminating in the recent takedowns.
Finland authorities successfully took down Sipulitie, the country’s “leading drug marketplace” on the dark web. This operation, executed by Finnish Customs in collaboration with Swedish police, targeted servers operating on the Tor network since 2023.
While Sipulitie primarily catered to the Finnish market, it had extended its reach by offering services in English.
The takedown affected also Tsätti, a chat-based contraband site run by the same administrator, which had been operational since 2022.
One interesting fact is the depth of intelligence gathered: Finnish authorities claim to have uncovered the real identities not just of the administrator, but also of site moderators, vendors, and customers.
Alex Cosoi, chief security strategist at Bitdefender said:
They imagine if they do a tiny mistake, that police will bust their doors the next day. Which is not the case,
A month later, they do another OpSec mistake, and still, police doesn’t come. And they grow sloppy and make more mistakes.
Conclusions
If technology is used to make oneself anonymous and engage in illegal activities, and every step is executed perfectly, it becomes extremely difficult for law enforcement to track. However, mistakes are inevitable.
Moreover, on the internet, no matter how private something is stated to be, and despite various encryption techniques that even quantum computers struggle to break, one thing remains certain: everything still leaves traces. On the client (computer, smartphone), or the servers (where a website is hosted), internet provider, vpn provider.
Even if the encryption is strong, digital footprints can be pieced together to reveal surprising amounts of information.
The very act of communication, regardless of its content, generates metadata, which can be just as revealing as the message itself.
Photo by Kaur Kristjan on Unsplash.










Comments are closed.