As sarcastic as it sounds, even with all the ever-increasing data breaches and various attacks, we are seeing ‘improvement’ let’s say, in the OWASP Top 10.
About the top 10
The OWASP (Open Web Application Security Project) top 10 is widely recognized as one of the best guidelines for web developers. In cybersecurity, we have several guidelines that help us understand and assess vulnerability in various devices and attack vectors, one of the most important ones being attack mitre. While each framework typically focuses on different aspects, MITRE ATT&CK attempts to simulate the mindset and actions of threat actors, while other frameworks, such as OWASP, STRIDE, NIST, CIS, and others, provide a more formal and targeted approach.
Therefore, the OWASP Top 10 offers something more tangible and useful for developers.
It’s not something that guarantees security altogether, but by understanding the most common threats and mitigating them as much as possible in the development phase, we can imagine fewer data breaches, by a large degree. And only then we can leave the rest of the work to the cybersecurity specialists.
Worth noting that many of the significant data breaches are consistently featured among the OWASP top 10 incidents.
The current top 10
- A01:2021-Broken Access Control.
- A02:2021-Cryptographic Failures
- A03:2021-Injection
- A04:2021-Insecure Design
- A05:2021-Security Misconfiguration
- A06:2021-Vulnerable and Outdated Components
- A07:2021-Identification and Authentication Failures
- A08:2021-Software and Data Integrity Failures
- A09:2021-Security Logging and Monitoring Failures
- A10:2021-Server-Side Request Forgery
What changed?
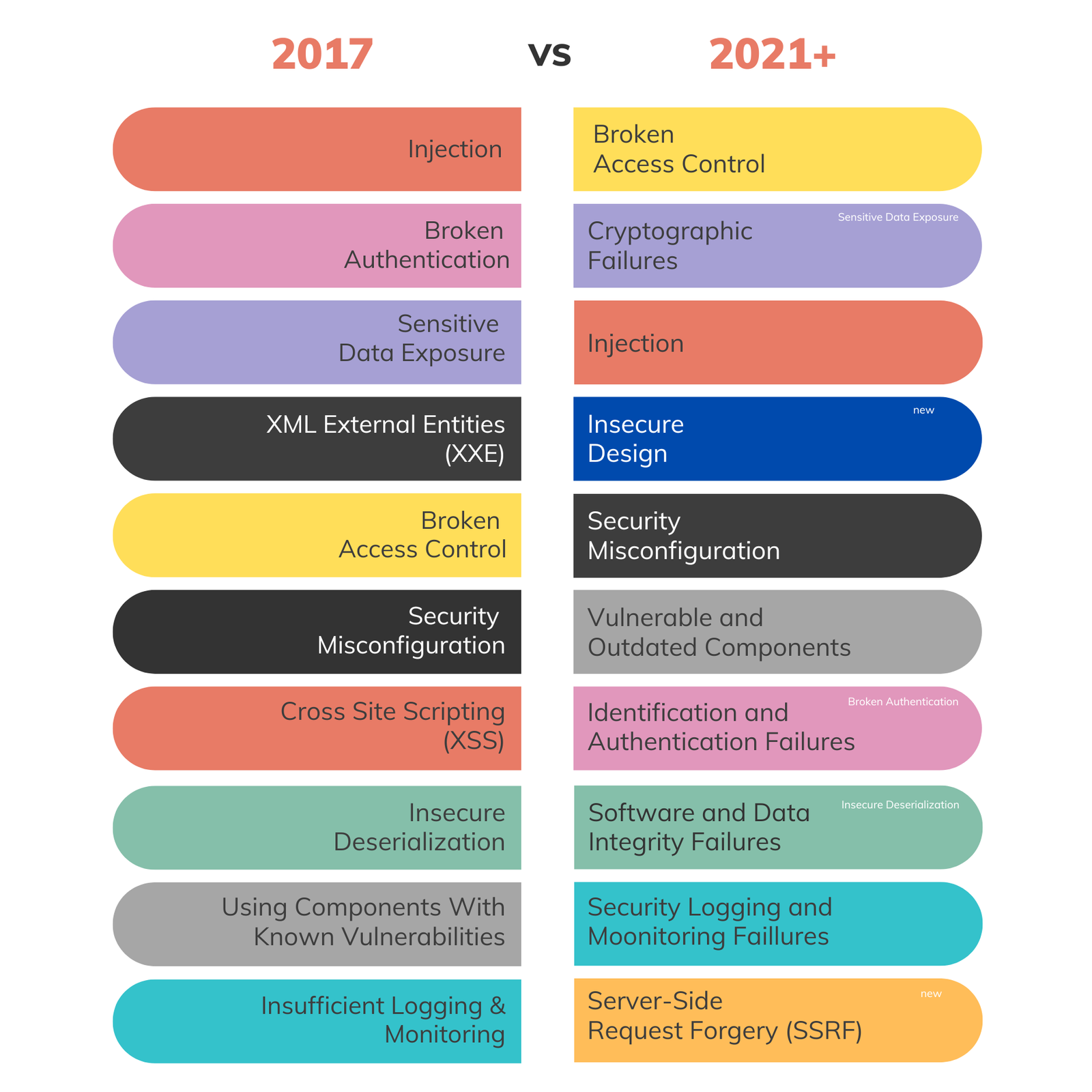
If the category changes or categories look a bit complicated, at a glance, no worries. We’ve all been confused when we tried to figure it out. We’ve tried to improve them a bit and sort them by using colors. So basically identical color meaning they are related.
What changed? Well, most things that make sense in this day and age. Grouping certain categories that contain similar vulnerabilities (ones that we marked with same color), while other new ones emerged, such as SSRF (Server-Side Request Forgery).
Rather than concentrating on every TOP 10 item, we will start a series, going into each item, where will write about their current state, with action points for protecting against them.
So why is this positive news?
Two categories that are much harder to solve now (Broken Access Control & Cryptographic Failures) are at the front of the list of popular vulnerabilities, replacing Injection which, for the first time in what, 20 years, is no longer #1. Injection is a vulnerability that’s relatively easy to prevent, and also to catch using static analysis methods.
So a high impact vulnerability that is easy to detect has many reliable methods to fix is still in the top 10 for so many years. We can all agree the state of web development could be a lot more secure. (I can point fingers since I spent more years developing websites than in school).
Under Injection we find cross-site-forgery, XSS, sql injection, and other methods allowing attackers to execute code on the victim’s browser, typically within web applications. Overall, a critical group of vulnerabilities.
While it’s still in the top 10, and arguably number #3 is also high, there is progress. Slow but progress.
The ones that are now #1 and #2 are, let’s say are more than deserving of their place.
- 1) Broken Access Control. Ensuring appropriate access control is a complex task, demanding not just technical challenges but also requires social awareness, and assessing and testing the entire app authentication & authorization logic.
- 2) Cryptographic Failures. Designing sound cryptography, a field of research where even veterans struggle, and putting it into practice correctly, is a game with high stakes where any mistake can be fatal. So it was a matter of time until we see it higher and higher in the list.
Conclusions
Overall, we would like to see Injection as low as possible, but this endeavor is something that cannot be done just with yearly pentesting and developing apps hoping for the best.
I’ve been a web developer for more than a decade, and I’m looking forward to a time when cybersecurity is just as important as following good coding rules and choosing the best way to build websites, like deciding between libraries and frameworks, using microservices vs monoliths, and so.
Looking forward to the day when we include cybersecurity analysis in the software development lifecycle, making it slightly harder for threat actors to steal and escape with personal data, and more.
Photo by Carlos Gonzalez.










Comments are closed.