The conventional thinking about password security often misses important nuances. While common sense trained us to believe “p#4St49@!” represents the pinnacle of security, the mathematics tells a more interesting story.
Spoiler: The longer the password, the better.
The Three Pillars of Password Security
1. Length
Password security’s math starts with a basic function.
|
1 2 3 4 5 6 7 8 9 |
C = c^L Where: C = Total possible combinations c = Character set size L = Password length |
This formula explains the security advantage of length:
- A 4-digit PIN: 10^4 = 10,000 combinations
- An 8-character complex password (92 symbols): 92^8 = essentially 5132188731375616 (5 million billion) combinations
- A 12-character alphanumeric password (62 characters): 62^12 = hard to even compute, 230 decimal digits combinations
Here’s a quick python representation:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
def password_combinations(charset_size: int, length: int) -> int: """ Args: charset_size (c): Size of character set length (L): Password length Returns: C: Total possible combinations """ return charset_size ** length # Example: PIN_SPACE = password_combinations(c=10, L=4) # 10,000 |
The complexity of cracking passwords grows exponentially as the length increases. Modern GPUs can crack complex passwords with 8 characters in about 8 hours. However, passwords that are longer and contain alphanumeric characters may take centuries to crack.
2. Entropy
Not all passwords of equal length are equally secure. Of course, the explanation is a bit more nuanced, because an important factor can be even the tool that is used to crack passwords and its approach to generate responses.
Consider these examples:
- “oooooooooooooo” (14 characters)
- “MyPasswordThis” (14 characters)
- “Kj9#mP2$vL5&nQ” (14 characters)
The length of the examples is the same, but their entropy, or randomness, differs a great deal between them.
Back to the examples:
- “oooooooooooooo” (little to no entropy. Despite being long, this password is incredibly easy to crack)
- “MyPasswordThis” (common language patterns, making it easy to be attacked using a dictionary, however, entropy increases drastically from a previous example)
- “Kj9#mP2$vL5&nQ” (example maximizes entropy by being unpredictable and simulating a sort of randomness)
3. Character Set Diversity
Increasing the number of character types enhances security, but not as much as boosting length or entropy. This often leads to predictable patterns, not to mention that it makes passwords harder to type, encouraging shorter lengths. The general algorithm’s complexity calculation is affected, essentially adding a variable to the function. For now, let’s put this aside; the increased complexity is mostly a matter of syntax, not substance.
Practical Usability
Password security exists on a spectrum of practicality:
- Daily Use Passwords (Like device encryption)
- “ALengthyAndMemorableEncryptionPassphrase”
- High length, moderate entropy, excellent memorability
- Password Manager Master Keys
- “the_cosmic_turtle_dances_at_midnight_472”
- Balanced length and memorability, good entropy
- Generated Passwords (Stored in password managers)
- “KZEEldaGkeOnYm9H4coe”
- Maximum entropy, no need for memorability
Real-World Attack Vectors
Password cracking software employs sophisticated strategies:
- Brute Force. Mathematical probability is still important for creating high-entropy passwords. A 12-character password, using both letters and numbers (62^12), forms a strong defense against brute force attacks.
- Dictionary Attacks. Pattern-based passwords like “ThisWhereIKeepMyMonay” face a different threat. Tools like hashcat use language patterns and common substitutions to crack seemingly complex passwords that follow linguistic rules.
Overall Generated Passwords Win
Password managers creating strings such as “KZEEldaGkeOnYm9H4coe” use cryptographically secure random number generators. This randomness defends against attacks using brute force or pattern recognition. Although its security depends on its storage and generation method, it’s the strongest in terms of password strength.
Practical Recommendations
- For Password Managers: Use generated passwords with maximum entropy
- For Master Passwords: Long, memorable phrases with some non-dictionary elements
- For Device Encryption: Extended passphrases that balance security and usability
Theis entire article could’ve been summarized by a xkcd comic:
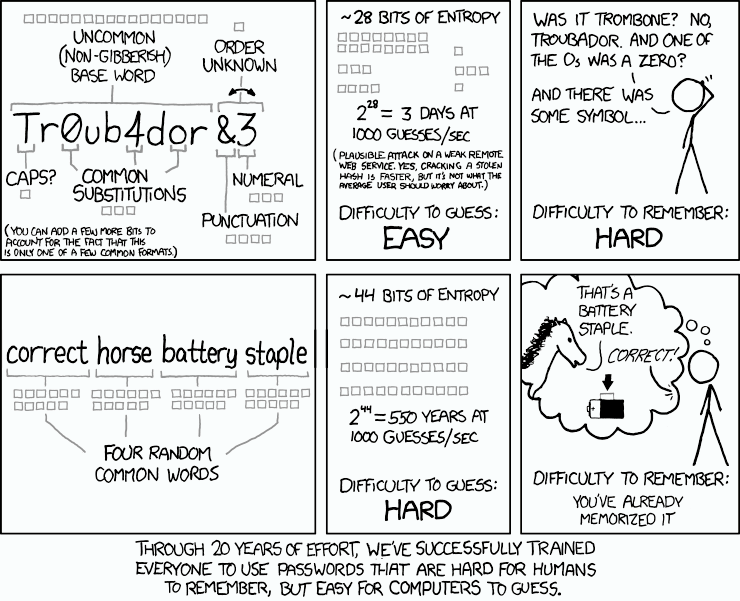
Photo by Volodymyr Kondriianenko on Unsplash.










Comments are closed.