It’s hard to weight risk. Is having your credentials on the dark web riskier than having your computer infected? We assume both are high, but for example having your computer infected demands immediate concern.
Which of the following activities are greater personal cybersecurity risk?
In one way or another, the risk is somewhat high on all of them. But as with everything, it depends. It depends on the shared information, on the breached website, and on the infected machine. We will try to rank them based on our opinion on risk factors.
1. Downloading software
Threat actors rely on infecting software as much as possible. So even a legitimate website can host legitimate software that, somewhere along the way, becomes a victim of a supply chain attack or a 0-day attack, we can only speculate, as examples happen constantly.
This risk is highest because usually getting a computer infected will give away a lot of private information and make it a ransomware, adware, or spyware victim. In ‘better’ cases, it becomes part of a botnet or is used for mining. I say ‘better‘ because it can be least damaging to personal data, but it’s not guaranteed.
A botnet can be as catastrophic if the computer or router that is infected, or other devices, are used to either DDoS attacks against for example government websites.
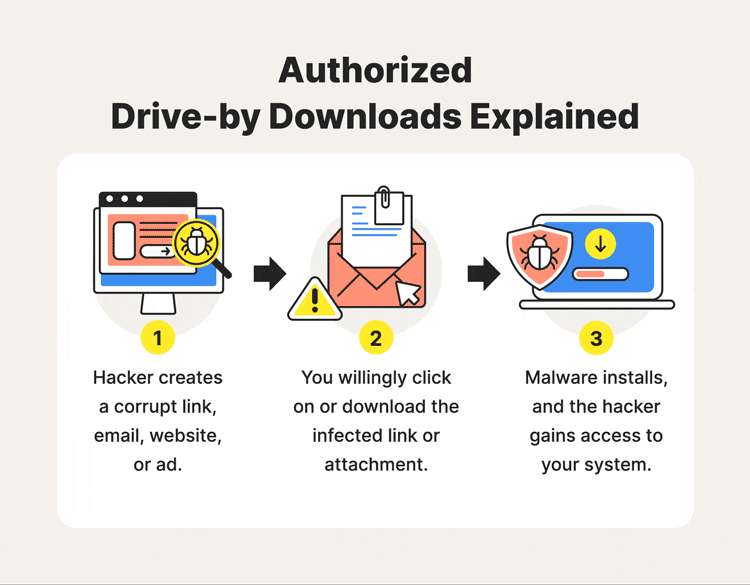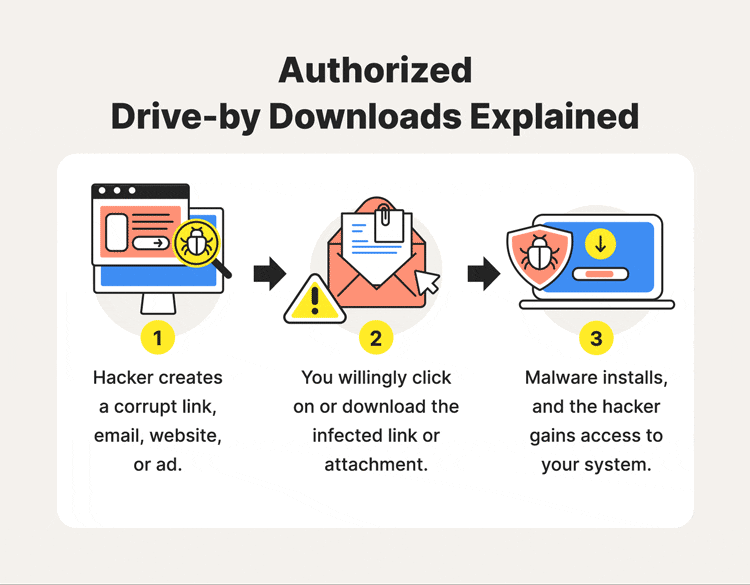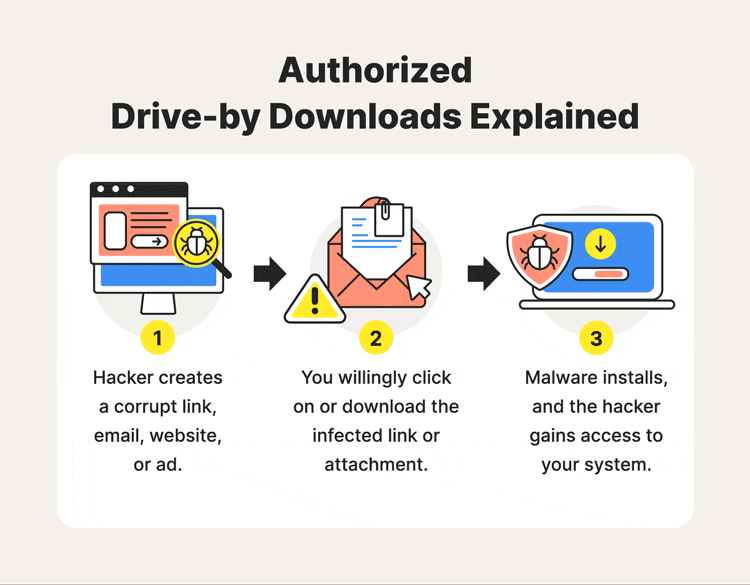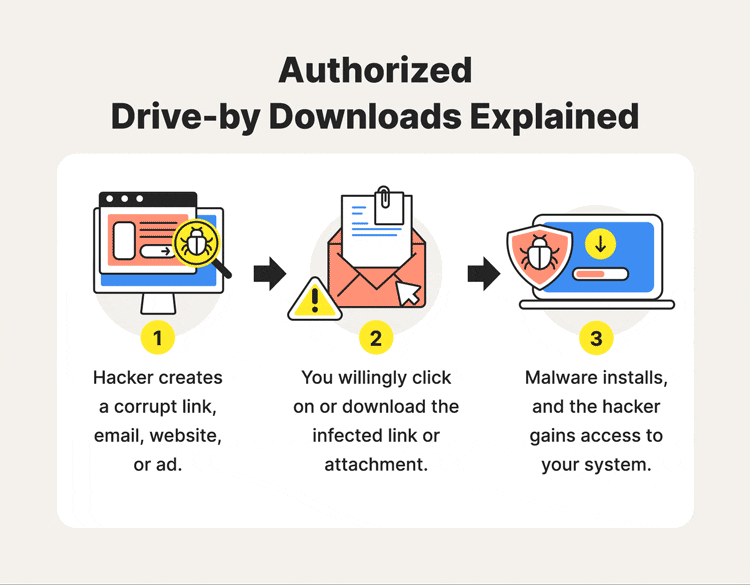
Photo source: Norton.
Ideally, treat software as a must-have necessity instead of a must-download abundance. Only download software that you truly need from trusted sources to minimize the risk of infection.
2. Wi-Fi networks and public Wi-Fi without VPN
It’s downright amazing, in my perspective, how much trust the majority has in public Wi-Fis, like those in hotels or Airbnb. While it can be said: “you can live your whole life connecting to public Wi-Fis and somehow manage to not get your info stolen,”, it’s improbable.
A VPN should be a mandatory tool, and now we can take a break like in a YouTube video and discuss NordVPN =). Just kidding, we are not sponsored.
Of course, as with any tool, research is required. Some say you want to trade privacy from Wi-Fi to the VPN provider. I am not entirely sure about that.
While learning ethical hacking, I ran various tests, and let me say this: “Without a VPN and while using an unprotected or public Wi-Fi, you can feel like a sitting duck.” Not sure why I quoted myself, but let’s go on.
Because of the amount of data I could just ‘listen‘ to while being connected to the Wi-Fi, and just seeing the other connected networks while using Kali Linux, it was an eye opening experience. If the user accesses (in 2024, I know) a non-HTTPS site, you can basically read everything like an open book.
There are a lot of security breaches and vulnerabilities that a VPN can protect against, such as man-in-the-middle attacks. With a laptop or any Wi-Fi-enabled device, you can act as the Wi-Fi for the connected user and become a ‘man in the middle.’ More complex is to say to the router, “I am the client,” and to say to the client, “I am the router.”

Photo source.
Usually, the Wi-Fi is the most important component of a network. If it gets infected or meddled with, the entire traffic that comes to it and goes outwards becomes vulnerable.
3. Weak and or reusing passwords

I did reuse passwords for a time.
I thought as a smart person, “I will use this password for only not-so-important sites, and in general, each site or important thing has its own password.” Important sites mean nothing anymore. Meta, for a while, stored plaintext passwords.
The best thing here is to just generate a very strong password using Chrome or your favorite browser and recover the password if forgotten. An even better approach is to periodically reset passwords.
You may never know how much info is already about you on the dark web. But you can find out…
4. Getting phished (social media, or by email at work)
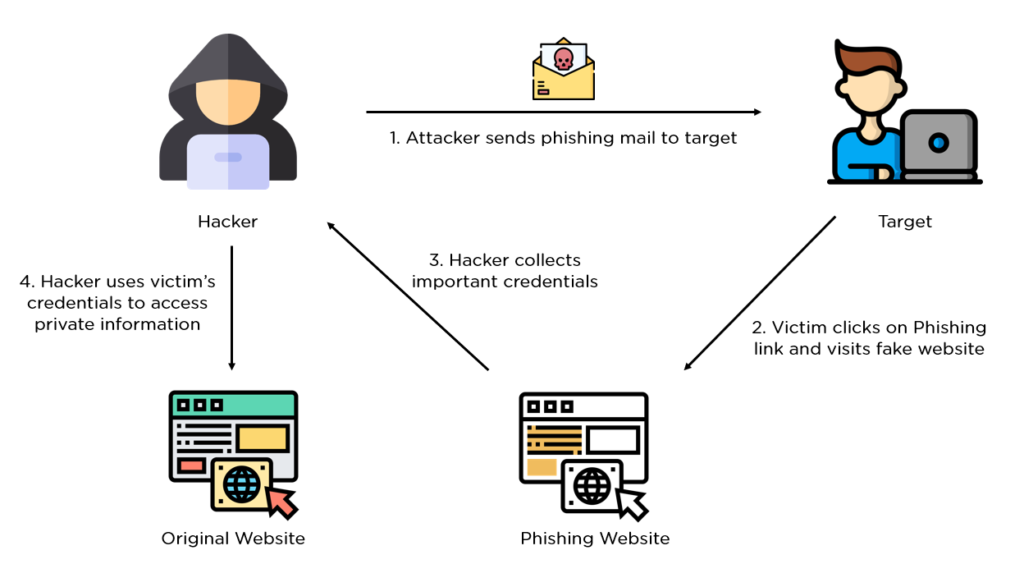
Photo source: simplilearn.com
It can happen. For example, on Facebook with the use of LLMs, hackers become more sophisticated in conversation. And it’s something big, a game changer.
We rarely encounter “click here to download, I promise it is not a virus,” anymore, now you get all sorts of messages that may easily misguide you, official-sounding, with all the engineering required to deceive.
And you don’t have to be a “stupid” person to fall for it, no one is stupid for clicking, they are deceived.
You, as well as I, can be easily deceived after a long day at work. You access the email, “Oh, what is this, another email? Let me read it fast,” and very easily fall into a trap.
5. Giving personal details with every occasion
I feel guilty about this, but I started to change my approach. Maybe not every site needs your birthday. Maybe unless you constantly buy from something, your addresses should not be pinpointed exactly. Maybe the personal email address that you use for banking and recovering various important accounts should not be used on all sign-ups. Secondary emails are the best for that, no one should know your primary email, and if they do, it’s at risk.
6. Oversharing information publicly
This is hard to quantify in terms of risk, and it may apply mostly if you are being targeted. Lower chances than random phishing, but still, providing too much information on public media, everyone agrees it’s something that can cause more harm than good. Vacations can be announced after they are done.
There’s no need to send dozens of stories to let people know that you are not at home and are basically in another country for a few days. This sounds paranoid, but if nothing else, learning cybersecurity has made me even more paranoid.
Featured photo by Pixabay







Comments are closed.