Patch Unavailable for End-of-Life Devices: What D-Link Owners Must Know
Security researcher ‘Netsecfish‘ recently uncovered a critical security issue affecting multiple older D-Link NAS (Network Attached Storage) devices.
This serious flaw, tracked as CVE-2024-3273, resides in the ‘/cgi-bin/nas_sharing.cgi‘ script and combines two alarming issues, CWE-77 (Command Injection), and CWE-798 (Use of Hard-coded Credentials):
The Backdoor
Hardcoded credentials (user=messagebus, empty password) provide easy entry for unauthorized individuals.
A simple HTTP request can grant unauthorized access:
|
1 |
GET /cgi-bin/nas_sharing.cgi?user=messagebus&passwd= |
Command Injection
The system parameter accepts commands with insufficient filtering. This means attackers could potentially execute commands on your NAS from anywhere with an internet connection.
Encode a command in base64, add it to the system parameter, and afterwards, worst case scenario:
|
1 |
GET /cgi-bin/nas_sharing.cgi?user=messagebus&passwd=&cmd=15&system=<BASE64_ENCODED_COMMAND> |
Affected Devices
As seen in the screenshot from github, more than 92000 of these vulnerable devices are directly accessible online, creating a widespread risk.
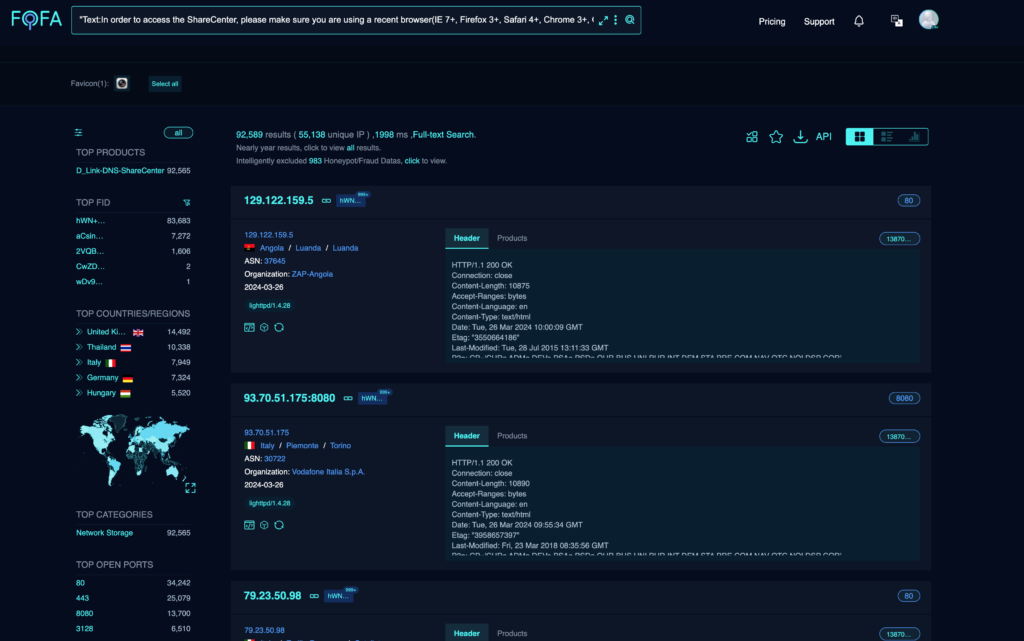
- DNS-320L (Versions 1.11, 1.03.0904.2013, 1.01.0702.2013)
- DNS-325 (Version 1.01)
- DNS-327L (Versions 1.09, 1.00.0409.2013)
- DNS-340L (Version 1.08)
The Impact
Imagine the worst, and bingo: data theft, system takeover, or adding the device into an existing botnet.
Recommendation
Patch Immediately, of course. But if the product has achieved end of life software support, unfortunately all we can say is ‘replace the NAS’.
But since this is not the first case, only a common occurrence, reconsider trusting and using this device. It might be time to consider alternative vendors for future NAS needs.







