Cybersecurity experts have uncovered a new series of phishing attacks, made using a sophisticated malware known as StrelaStealer. These attacks have affected over 100 entities across the European Union and the United States, as reported by the Palo Alto Networks Unit 42 team.
One notable characteristic of the StrelaStealer malware is using a polyglot file infection method to evade detection.
A Word About Polyglots
In security context, a Polyglot is simply a file that is created by combining at least two file formats together in such a way that each format can be interpreted individually. There are examples of JAR files that can be combined with MSI, or PPT and JS, GIF and JS, etc. Therefore the file would have a different behavior depending on the application the user used to open or execute it.
Because of this aspect, polyglots are usually considered a hacker’s best friend. Files can be manipulated by attackers to avoid being detected by anti-malware systems that rely only on file format identification. In general, the technique involves executing the same file twice in the infection process. The first execution exhibits ‘safe’ activities, while the second execution carries out malicious intent.
More on StrelaStealer Cyber Attack
Originally identified in November 2022, StrelaStealer has the capability to extract email credentials from prominent email applications and send this sensitive information to a server under the attackers’ control.
Targeting the Windows environments, the StrelaStealer malware has evolved over time, but the spreading method remains the same: through email, spreading via attachments.
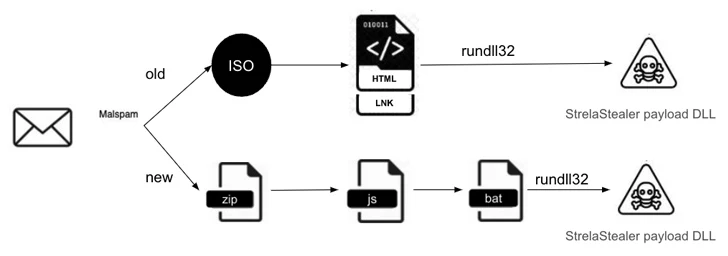
In these phishing attacks, when the victims opens one of these ZIP files, they will find a JavaScript file inside. Executing this JavaScript file triggers the download or creation of a batch file (.bat). If this batch file is then executed, it will initiate the StrelaStealer malware, and afterwards the ‘fun’ starts.
The malware relies on the usage of rundll32.exe, which is a legitimate program included with Windows. Normally, rundll32.exe is used to run various functions stored in DLL (Dynamic-Link Library). But, in this case, the malware proceeds to steal information, such as email login credentials.
Cybersecurity researchers have found two major waves of StrelaStealer attacks, one in November 2023 and the second one in January 2024, targeting all major sectors within the E.U. and the U.S. Each time the code and files used to infect, changed.
Therefore, we should expect a new attack soon, and prepare for it!
How to Defend
Defending against StrelaStealer, like against most phishing-based threats, involves a combination of technical measures, but more importantly user education should not be neglected. Here are some key strategies:
– Application Whitelisting: Configure the systems to only allow approved applications to run, which can prevent malware from executing.
– Least Privilege Access: This ensures that users and applications have only a limited access depending on their need to avoid widespread and company-wide data breaches.
– User Training & Simulation Exercises







Comments are closed.