A massive , long going botnet known as “Raptor Train” has been disrupted by the FBI in a court-authorized operation, ending a four-year long campaign of cyber intrusion. This appears to be orchestrated by Chinese state-sponsored hackers.
The botnet, is believed to have infected small office/home office (SOHO) routers, IP cameras, digital video recorders (DVRs), and network-attached storage (NAS) devices across the globe, more prevalent in US and EU. This botnet was controlled by a Beijing-based company called Integrity Technology Group, and was identified in the cybersecurity community as “Flax Typhoon“.
This operation leveraged a variant of the Mirai malware, dubbed “Nosedive,” which infiltrated a sheer number of vulnerable IoT devices worldwide. The compromised devices were connected through a three-tiered architecture managed by an online application known as “Sparrow”, in turn allowing the hackers to execute commands, upload and download files, and potentially launch distributed denial-of-service (DDoS) attacks while disguising their activities as routine internet traffic.
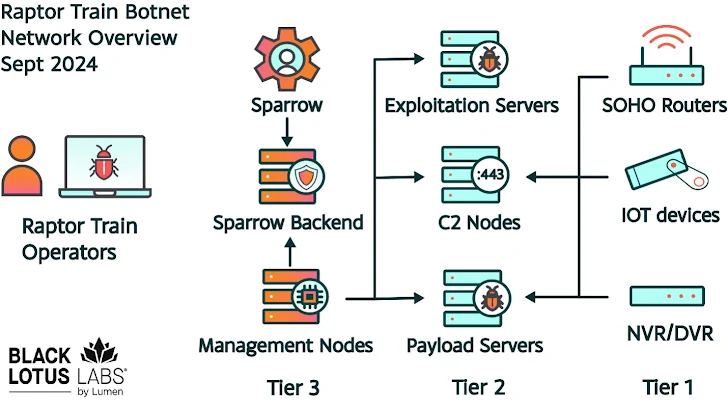
Photo source: lumen.com
Despite the thread actors using a DDoS attack on the bureau’s operational infrastructure, the takedown was successful. The FBI seized control of the botnet’s command-and-control (C2) servers and issued disabling commands to the malware on infected devices.
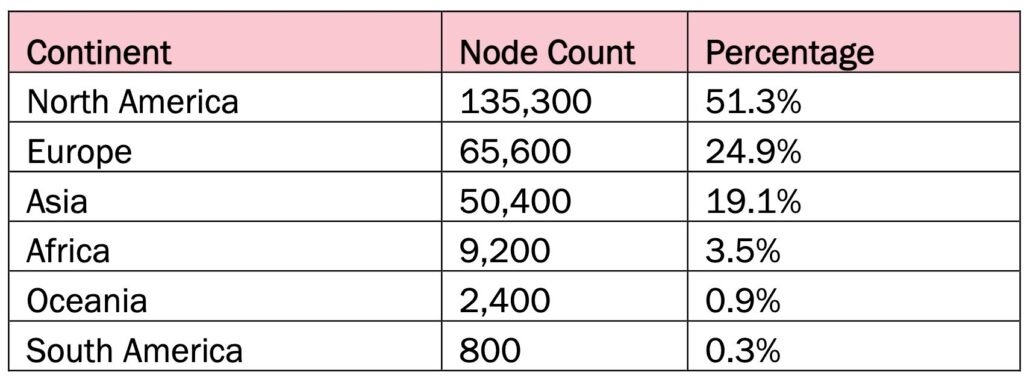
The operation revealed that the botnet had a significant global footprint. In June 2024, the botnet encompassed over 260,000 devices, with victims primarily located in North America (approximately 135,300 devices), Europe (65,600), and Asia (50,400).
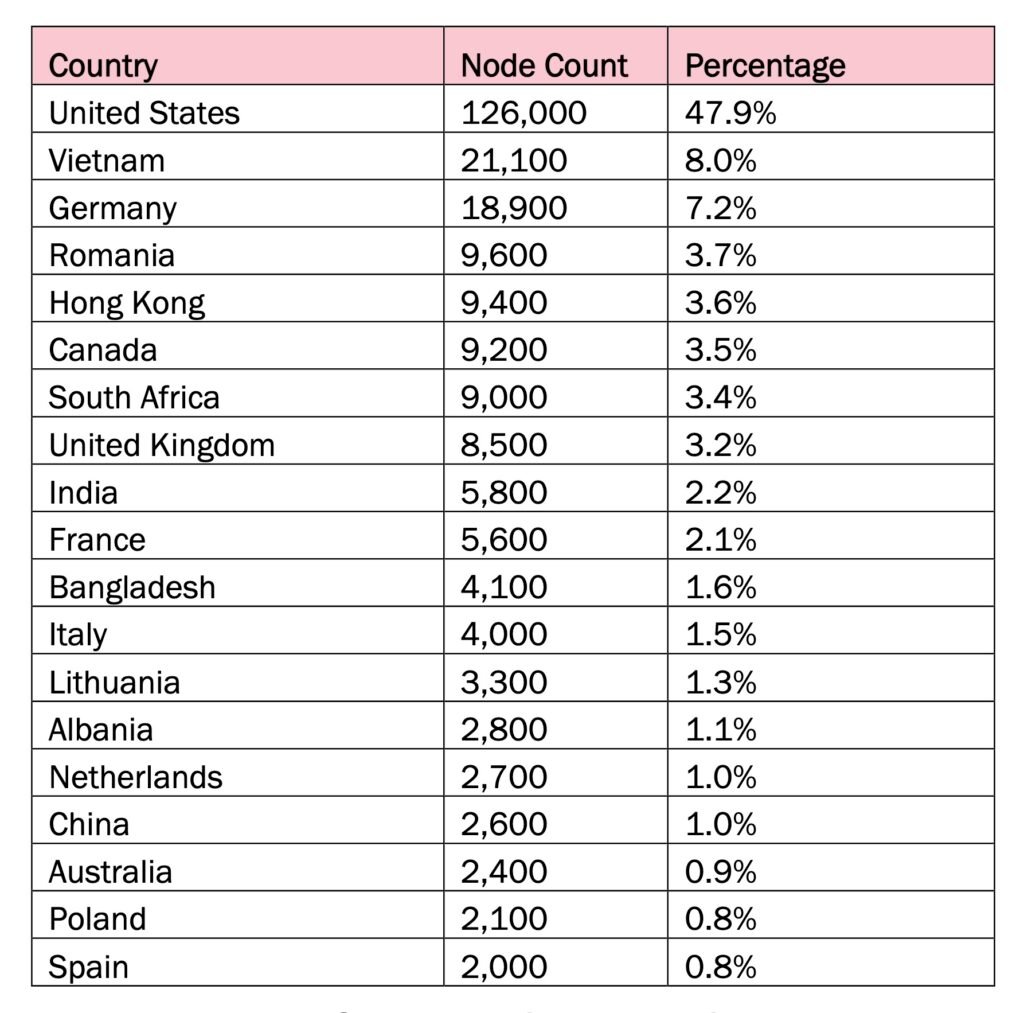
Countries most affected included the United States, Taiwan, Vietnam, Brazil, Hong Kong, and Turkey.
Conclusions & Safety Tips
There’s a saying that tech people love analog and run from IoT devices. While this isn’t entirely true for me, I do maintain a very cautious approach to these devices.
Firstly, if a device doesn’t absolutely need internet access, don’t connect it. Limiting unnecessary connectivity reduces potential vulnerabilities.
Secondly, IoT devices should, if possible, be placed on an IoT-only network. This way, you can apply the principle of least privilege while also keeping a monitoring tool on them. However, while an IoT network helps, it doesn’t fully protect you if the device is hijacked and used as part of a botnet or for DDoS attempts or traffic routing.
Thirdly, if an IoT device needs internet access, I usually connect it through a VPN that is connected to the IoT network. This reduces exposure by preventing the device from being directly exposed to the internet, especially if it has weak security features. Connecting through a VPN helps hide its IP address and reduces exposure to external threats, and it also helps prevent eavesdropping on encrypted traffic.
Lastly, update every router and device regularly. Reboot them if the monitoring tool shows excessive traffic and you’re not doing anything. This could mean the device is infected.
The most important tool in any household is the router. Protect it, you don’t have to be a tech guru to add a VPN or a firewall to your router.
Photo by Jakub Zerdzicki: https://www.pexels.com/photo/smart-home-android-17018384/








Comments are closed.